之前在NSSCTF题库找题的时候无意中翻到了一套取证题,一个镜像13问。粗略扫了一下,似乎是有关勒索病毒的内存取证,看起来挺有意思的,顺手做一做。
现在咱做内存取证主要还是用volatility。memprocfs看起来很方便,但用得不太习惯。之后再熟悉一下吧。
0x01 What the Password
you got a sample of rick’s PC’s memory. can you get his user password?
第一问就是问内存镜像中的账户密码。用hashdump看一下。
vol -f OtterCTF.vmem windows.hashdump
Volatility 3 Framework 2.5.0 Progress: 100.00 PDB scanning finished User rid lmhash nthash Administrator 500 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0 Guest 501 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0 Rick 1000 aad3b435b51404eeaad3b435b51404ee 518172d012f97d3a8fcc089615283940
可以看到有一个Rick账户。nthash查表查不出来,只说明账户用的还不算是弱密码。这种情况下很难从哈希值获取密码了,但明文密码可能还缓存在lsa进程中。再用lsadump试一下。
vol -f OtterCTF.vmem windows.lsadump
Key Secret Hex DefaultPassword (MortyIsReallyAnOtter 28 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 4d 00 6f 00 72 00 74 00 79 00 49 00 73 00 52 00 65 00 61 00 6c 00 6c 00 79 00 41 00 6e 00 4f 00 74 00 74 00 65 00 72 00 00 00 00 00 00 00 00 00 ...
这样就直接取出来明文密码了。
NSSCTF{MortyIsReallyAnOtter}
0x02 General Info
Let’s start easy - whats the PC’s name and IP address?
这题是问内存镜像的主机名和IP地址。简单用netscan扫描一下网络连接
vol -f OtterCTF.vmem windows.netscan
... 0x7e5228d0 TCPv4 192.168.202.131 50075 70.65.116.120 52700 CLOSED 2836 BitTorrent.exe - 0x7e52f010 TCPv4 192.168.202.131 50343 86.121.4.189 46392 CLOSED 2836 BitTorrent.exe - 0x7e563860 TCPv4 192.168.202.131 50170 103.232.25.44 25384 CLOSED 2836 BitTorrent.exe - 0x7e572cf0 TCPv4 192.168.202.131 50125 122.62.218.159 11627 CLOSED 2836 BitTorrent.exe - 0x7e5d6cf0 TCPv4 192.168.202.131 50324 54.197.8.177 49420 CLOSED 2836 BitTorrent.exe - ...
localaddress中的ipv4地址除了127.0.0.1和0.0.0.0之外就是192.168.202.131了,显然这个就是主机ip地址。
而主机名可以直接从用户进程的环境变量中查到,要比翻注册表快捷得多。指定一个chrome进程的pid看看envars
vol -f OtterCTF.vmem windows.envars --pid=4076
... 4076 chrome.exe 0x401e40 CommonProgramW6432 C:\Program Files\Common Files 4076 chrome.exe 0x401e40 COMPUTERNAME WIN-LO6FAF3DTFE 4076 chrome.exe 0x401e40 ComSpec C:\Windows\system32\cmd.exe ... 4076 chrome.exe 0x401e40 TMP C:\Users\Rick\AppData\Local\Temp 4076 chrome.exe 0x401e40 USERDOMAIN WIN-LO6FAF3DTFE 4076 chrome.exe 0x401e40 USERNAME Rick ...
环境变量COMPUTERNAME和USERDOMAIN的值都是WIN-LO6FAF3DTFE,那这个一定就是主机名了。
NSSCTF{WIN-LO6FAF3DTFE-192.168.202.131}
0x03 Play Time
Rick just loves to play some good old videogames. can you tell which game is he playing? whats the IP address of the server?
这道题问的是Rick玩的一个电子游戏和游戏服务器的ip地址。那就再翻一翻pslist和netscan吧,找一找有什么看起来像电脑游戏的进程。
vol -f OtterCTF.vmem windows.pslist
... 2836 2728 BitTorrent.exe 0xfa801b290b30 24 471 1 True 2018-08-04 19:27:07.000000 N/A Disabled 2844 2728 WebCompanion.e 0xfa801b2f02e0 0 - 1 False 2018-08-04 19:27:07.000000 2018-08-04 19:33:33.000000 Disabled 3064 492 SearchIndexer. 0xfa801b3aab30 11 610 0 False 2018-08-04 19:27:14.000000 N/A Disabled 2308 2836 bittorrentie.e 0xfa801b4a7b30 15 337 1 True 2018-08-04 19:27:19.000000 N/A Disabled 2624 2836 bittorrentie.e 0xfa801b4c9b30 13 316 1 True 2018-08-04 19:27:21.000000 N/A Disabled 708 2728 LunarMS.exe 0xfa801b5cb740 18 346 1 True 2018-08-04 19:27:39.000000 N/A Disabled 724 492 PresentationFo 0xfa801988c2d0 6 148 0 False 2018-08-04 19:27:52.000000 N/A Disabled 412 492 mscorsvw.exe 0xfa801b603610 7 86 0 True 2018-08-04 19:28:42.000000 N/A Disabled 164 492 svchost.exe 0xfa801a6af9f0 12 147 0 False 2018-08-04 19:28:42.000000 N/A Disabled 3124 492 mscorsvw.exe 0xfa801a6c2700 7 77 0 False 2018-08-04 19:28:43.000000 N/A Disabled 3196 492 svchost.exe 0xfa801a6e4b30 14 352 0 False 2018-08-04 19:28:44.000000 N/A Disabled 4076 2728 chrome.exe 0xfa801a4e3870 44 1160 1 False 2018-08-04 19:29:30.000000 N/A Disabled 4084 4076 chrome.exe 0xfa801a4eab30 8 86 1 False 2018-08-04 19:29:30.000000 N/A Disabled 576 4076 chrome.exe 0xfa801a502b30 2 58 1 False 2018-08-04 19:29:31.000000 N/A Disabled 1808 4076 chrome.exe 0xfa801a4f7b30 13 229 1 False 2018-08-04 19:29:32.000000 N/A Disabled 3924 4076 chrome.exe 0xfa801aa00a90 16 228 1 False 2018-08-04 19:29:51.000000 N/A Disabled 2748 4076 chrome.exe 0xfa801a7f98f0 15 181 1 False 2018-08-04 19:31:15.000000 N/A Disabled 3820 2728 Rick And Morty 0xfa801b486b30 4 185 1 True 2018-08-04 19:32:55.000000 N/A Disabled 3720 3820 vmware-tray.ex 0xfa801a4c5b30 8 147 1 True 2018-08-04 19:33:02.000000 N/A Disabled 3880 1484 WebCompanionIn 0xfa801b18f060 15 522 0 True 2018-08-04 19:33:07.000000 N/A Disabled 3648 4076 chrome.exe 0xfa801a635240 16 207 1 False 2018-08-04 19:33:38.000000 N/A Disabled 1796 4076 chrome.exe 0xfa801a5ef1f0 15 170 1 False 2018-08-04 19:33:41.000000 N/A Disabled 3208 3880 sc.exe 0xfa801b08f060 0 - 0 False 2018-08-04 19:33:47.000000 2018-08-04 19:33:48.000000 Disabled 452 3880 sc.exe 0xfa801aeb6890 0 - 0 False 2018-08-04 19:33:48.000000 2018-08-04 19:33:48.000000 Disabled 3504 3880 sc.exe 0xfa801aa72b30 0 - 0 False 2018-08-04 19:33:48.000000 2018-08-04 19:33:48.000000 Disabled 2028 3880 sc.exe 0xfa801ac01060 0 - 0 False 2018-08-04 19:33:49.000000 2018-08-04 19:34:03.000000 Disabled 3496 492 Lavasoft.WCAss 0xfa801aad1060 14 473 0 False 2018-08-04 19:33:49.000000 N/A Disabled 3856 3880 WebCompanion.e 0xfa801a6268b0 15 386 0 True 2018-08-04 19:34:05.000000 N/A Disabled 3304 3132 notepad.exe 0xfa801b1fd960 2 79 1 False 2018-08-04 19:34:10.000000 N/A Disabled 3916 1428 cmd.exe 0xfa801a572b30 0 - 0 False 2018-08-04 19:34:22.000000 2018-08-04 19:34:22.000000 Disabled
乱七八糟的进程。但其实进程数还不算很多,先想办法排除一下。除了chrome.exe浏览器和bittorrent.exe下载器之外,有个Rick And Morty开头的进程,但仔细看看netscan的输出,这个进程并没有建立网络连接,那大概就不是了。还有几个Lavasoft的进程,搜了一下似乎是个杀毒软件,并不是游戏。
除此之外有个LunarMS.exe的进程,也确实和某个外部ip地址建立过TCP连接,那大概这个就是那个电脑游戏了,虽然咱到最后也没弄清楚这个游戏具体是个啥
vol -f OtterCTF.vmem windows.netscan
Offset Proto LocalAddr LocalPort ForeignAddr ForeignPort State PID Owner Created 0x7d42ba90 TCPv4 - 0 56.219.196.26 0 CLOSED 2836 BitTorrent.exe N/A 0x7d60f010 UDPv4 0.0.0.0 1900 * 0 2836 BitTorrent.exe 2018-08-04 19:27:17.000000 0x7d6124d0 TCPv4 192.168.202.131 49530 77.102.199.102 7575 CLOSED 708 LunarMS.exe - 0x7d62b3f0 UDPv4 192.168.202.131 6771 * 0 2836 BitTorrent.exe 2018-08-04 19:27:22.000000 0x7d62d690 TCPv4 192.168.202.131 49229 169.1.143.215 8999 CLOSED 2836 BitTorrent.exe N/A 0x7d62f4c0 UDPv4 127.0.0.1 62307 * 0 2836 BitTorrent.exe 2018-08-04 19:27:17.000000 0x7d62f920 UDPv4 192.168.202.131 62306 * 0 2836 BitTorrent.exe 2018-08-04 19:27:17.000000 ...
服务器ip地址是77.102.199.102,试着交一下flag。
NSSCTF{LunarMS-77.102.199.102}
0x04 Name Game
We know that the account was logged in to a channel called Lunar-3. what is the account name?
Rick的游戏账户登录到了一个名叫’Lunar-3’的频道,让咱找到Rick的游戏账户名。
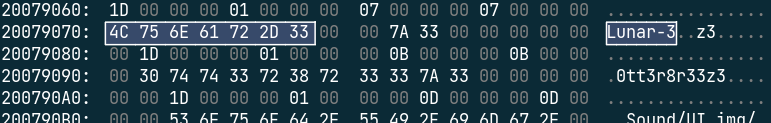
这个想不到什么好的方法。注册表和剪切板里也没缓存Rick的游戏用户名,那用户名只可能在进程内存里了。题目既然提到了Lunar-3。试试把LunarMS.exe的进程内存整个dump出来用16进制编辑器查找一下看看。
vol -f OtterCTF.vmem windows.memmap --pid 708 --dump
还真让咱给找到了。
那用户名应该就是0tt3r8r33z3了,试着交一下flag。
NSSCTF{0tt3r8r33z3}
0x05 Name Game 2
From a little research we found that the username of the logged on character is always after this signature. What’s rick’s character’s name?
已知登录了的角色名在内存中储存的规律:
0x64 0x??{6-8} 0x40 0x06 0x??{18} 0x5a 0x0c 0x00{2}
让咱找Rick的游戏角色的角色名。
那就把游戏的进程内存用re扫一遍看看。
import remem_pattern = rb"\x64.{6,8}\x40\x06.{18}\x5a\x0c\x00\x00.{16}" with open ("pid.708.dmp" , "rb" ) as f: print (re.findall(mem_pattern, f.read()))
[b'd\x00\x00\x00\x00\x00\x00@\x06\x00\x00\xb4\xe5\xaf\x00\x01\x00\x00\x00\x00\x00\x00\x00\xb0\xe5\xaf\x00Z\x0c\x00\x00M0rtyL0L\x00\x00\x00\x00\x00\x00\x00!']
输出了一行匹配到的数据。对应出现的位置,角色名就是”M0rtyL0L”
NSSCTF{M0rtyL0L}
0x06 Silly Rick
Silly rick always forgets his email’s password, so he uses a Stored Password Services online to store his password. He always copy and paste the password so he will not get it wrong. whats rick’s email password?
rick习惯用剪贴板复制密码,让咱找回邮箱密码。
那这就很简单了,直接用volatility2
volatility_2.6 _win64_standalone.exe -f .\OtterCTF.vmem --profile =Win7SP1x64 clipboard
Session WindowStation Format Handle Object Data ---------- ------------- ------------------ ------------------ ------------------ -------------------------------------------------- 1 WinSta0 CF_UNICODETEXT 0x602e3 0xfffff900c1ad93f0 M@il_Pr0vid0rs 1 WinSta0 CF_TEXT 0x10 ------------------ 1 WinSta0 0x150133L 0x200000000000 ------------------ 1 WinSta0 CF_TEXT 0x1 ------------------ 1 ------------- ------------------ 0x150133 0xfffff900c1c1adc0
NSSCTF{M@il_Pr0vid0rs}
0x07 Hide And Seek
The reason that we took rick’s PC memory dump is because there was a malware infection. Please find the malware process name (including the extension)
题目提到Rick的电脑里有个恶意程序,让咱给它的进程名找出来。
之前有个Rick And Morty season 1 download.exe的进程非常可疑。试着直接交一下flag结果并不正确。之后用virustotal查一下也没有报毒。
再用pstree看一下进程列表,
vol -f OtterCTF.vmem windows.pstree
... * 3820 2728 Rick And Morty 0xfa801b486b30 4 185 1 True 2018-08-04 19:32:55.000000 N/A ** 3720 3820 vmware-tray.ex 0xfa801a4c5b30 8 147 1 True 2018-08-04 19:33:02.000000 N/A * 2804 2728 vmtoolsd.exe 0xfa801b1cdb30 6 190 1 False 2018-08-04 19:27:06.000000 N/A ...
可以发现Rick And Morty season 1 download.exe下有一个vmware-tray.exe子进程。真正的vmware托盘程序应该是vmtoolsd.exe。那这个肯定就是伪装进程名的恶意程序了。dump下来用virustotal扫一下,立刻就报毒了,勒索程序。
NSSCTF{vmware-tray.exe}
0x08 Path To Glory
How did the malware got to rick’s PC? It must be one of rick old illegal habits…
病毒是Rick And Morty season 1 download.exe放出的,明显是bt下动画片下到了这个exe之后直接双击运行中招的。题目提到的illegal habits大概也就指的是bt下载。但搞不清楚题目是在问什么。
到处翻了翻都没有什么结果,索性filescan了一下。
vol -f OtterCTF.vmem windows.filescan
可以扫到下载下来的几个mkv动画片,应该还算和种子下载相关。
vol -f OtterCTF.vmem windows.dumpfiles --physaddr 0x7d6b3a10 ... vol -f OtterCTF.vmem windows.dumpfiles --physaddr 0x7dae9350
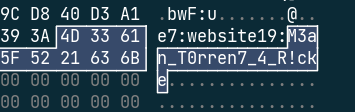
把视频文件挨个filedump下来,但是都打不开了。又dump了种子文件。最后在\Users\Rick\AppData\Roaming\BitTorrent\Rick And Morty season 1 download.exe.1.torrent种子文件里找到了flag。
NSSCTF{M3an_T0rren7_4_R!ck}
0x09 Bit 4 Bit
We’ve found out that the malware is a ransomware. Find the attacker’s bitcoin address.
问勒索程序的比特币地址。
上网简单搜了一下,比特币地址的表示不止一种,都是类似于Base的编码,不太好用正则匹配。那就先先把勒索程序的exe给filedump下来。
vol -f OtterCTF.vmem windows.dumpfiles --physaddr 0x7dc6cf20
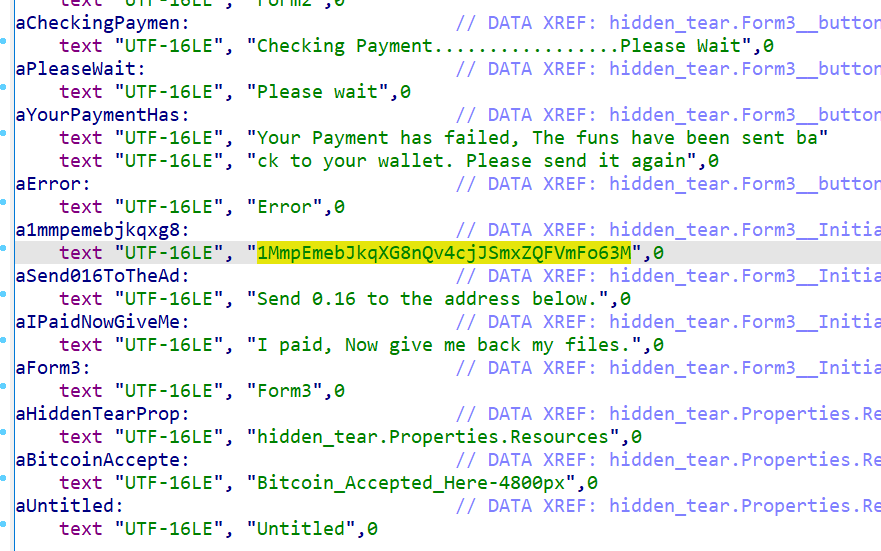
小心地把勒索程序拖进IDA。在Data区可以直接看到字符串,有一段Base编码的字符,就是P2PKH格式的比特币地址。
NSSCTF{1MmpEmebJkqXG8nQv4cjJSmxZQFVmFo63M}
0x0A Graphic’s For The Weak
There’s something fishy in the malware’s graphics.
简单把勒索软件进程整个进程内存dump下来,foremost一下就可以找到进程中的图片了。
vol -f OtterCTF.vmem windows.memmap --pid 3720 --dump foremost ./pid.3720.dmp
NSSCTF{S0_Just_M0v3_Socy}
0x0B Recovery
Rick got to have his files recovered! What is the random password used to encrypt the files?
找密码。
勒索程序被IDA解析来的函数名都是hidden_tear开头的。网上查了一下,这玩意居然是个开源的勒索病毒组件…简直丧心病狂
https://github.com/goliate/hidden-tear
这下逆都不用逆了。直接翻源码。
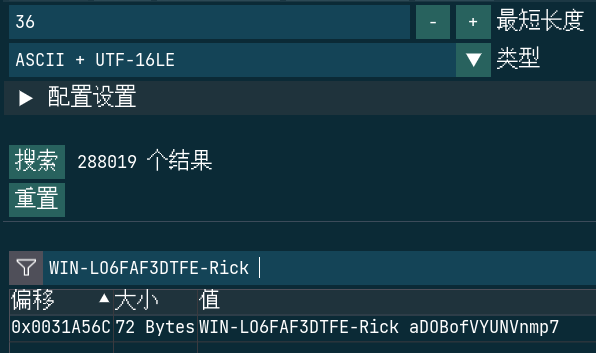
README就写了这玩意的运作方式。随机生成密码,把密码通过网络发送到勒索者的服务器,然后以密码的sha256值产生PBKDF2密钥对指定后缀名的文件进行AES加密。发送密码的格式是computerName+"-"+userName+" "+password。密码长度是15字节,紧接在WIN-LO6FAF3DTFE-Rick 后,整个串共36字节。在进程内存里查找一下就行。注意编码要用UTF16LE
NSSCTF{aDOBofVYUNVnmp7}
0x0C Closure
Now that you extracted the password from the memory, could you decrypt rick’s files?
用密码解密文件。
首先要从内存中获取加密的文件。在之前filscan的结果里找一找,可以发现桌面上有一个Flag.txt,显然就是咱要看的文件。用vol把它先dump出来。
... 0x7e410890 \Users\Rick\Desktop\Flag.txt 216 ...
vol -f OtterCTF.vmem -o /data/share windows.dumpfiles --physaddr 0x7e410890
然后就想办法弄个用来解密的程序。套壳勒索程序,用的加密方法应该还是hidden_tear里的。直接仿照着hidden_tear源代码的加密方法改个解密方法出来,用密码解一下。
https://github.com/goliate/hidden-tear/blob/master/hidden-tear/hidden-tear/Form1.cs
using System;using System.IO;using System.Text;using System.Security.Cryptography;namespace test { class test { static void Main () Decrypt d = new Decrypt(); d.decryptFile("file.0x7e410890.0xfa801b0532e0.DataSectionObject.Flag.txt.dat" , "aDOBofVYUNVnmp7" ); } } class Decrypt { public byte [] AES_Decrypt (byte [] bytesToBeDecrypted, byte [] passwordBytes byte [] decryptedBytes; byte [] saltBytes = new byte [] { 1 , 2 , 3 , 4 , 5 , 6 , 7 , 8 }; using (MemoryStream ms = new MemoryStream()){ using (RijndaelManaged AES = new RijndaelManaged()){ AES.KeySize = 256 ; AES.BlockSize = 128 ; AES.Mode = CipherMode.CBC; var key = new Rfc2898DeriveBytes(passwordBytes, saltBytes, 1000 ); AES.Key = key.GetBytes(AES.KeySize / 8 ); AES.IV = key.GetBytes(AES.BlockSize / 8 ); using (var cs = new CryptoStream(ms, AES.CreateDecryptor(), CryptoStreamMode.Write)){ cs.Write(bytesToBeDecrypted, 0 , bytesToBeDecrypted.Length); cs.Close(); } decryptedBytes = ms.ToArray(); } } return decryptedBytes; } public void decryptFile (string file, string password byte [] bytesToBeDecrypted = File.ReadAllBytes(file); byte [] passwordBytes = SHA256.Create().ComputeHash(Encoding.UTF8.GetBytes(password)); byte [] bytesDecrypted = AES_Decrypt(bytesToBeDecrypted, passwordBytes); System.IO.File.Copy(file, file+".unlocked" ); File.WriteAllBytes(file+".unlocked" , bytesDecrypted); } } }
NSSCTF{Im_Th@_B3S7_RicK_0f_Th3m_4ll}
感觉取证已经差不多了吧,越做越无聊了。本来也不是什么技术含量很高的东西,以后不用再花太多精力研究它了。